How Aws Cloud Backup can Save You Time, Stress, and Money.
Wiki Article
Aws Backup - An Overview
Table of ContentsThe Definitive Guide to Protection Against RansomwareWhat Does Ec2 Backup Mean?The 7-Minute Rule for S3 Cloud BackupMore About Aws BackupGetting The Ransomware Protection To WorkRto Things To Know Before You Buy

The GDPR stresses the individual data civil liberties of EU locals, including the right to transform, access, get rid of, or transfer their information. Individual information refers to any type of details that associates to an individual.
To maintain their data readily available whatsoever times, firms need to maintain the IT infrastructure energetic also when it comes to a disaster. This state of guaranteed accessibility to data is recognized as information accessibility. This write-up evaluates the essentials of data accessibility and also its difficulties, as well as offers methods to keep a high level of data schedule.
Without a proper data security plan, sensitive info can fall under the hands of attackers, enabling them to get to your network, as well as reveal the individual information of clients and also employees. This post presents the principle of data safety and security as well as the various devices and methods you can utilize to safeguard your data and also protect against a disaster.
3 Simple Techniques For Protection Against Ransomware
The inscribed info can only be decoded with an unique decryption trick. You can produce the essential either at the time of encryption or ahead of time. File encryption makes sure the integrity of information by securing it from unauthorized alteration. File encryption decreases the danger of accessing data from unreliable sources by verifying information's source.A constant information defense system maintains a record of all information changes and allows you to recover a system to any kind of previous moment. This type of back-up addresses the problem of losing information developed between 2 set up backups. It also supplies security versus strikes like ransomware or malware, along with unintentional deletion of data.
Any business that processes as well as shops individual information of EU people, also if it is not literally situated in the EU, must apply to the GDPR guidelines. There are 2 main duties in the GDPR: the GDPR Information Cpu is an entity that holds or refines this type of data in support of another organization, and a GDPR Information Controller that gathers or processes personal data for its own purposes.
Immutable S3 things are secured using things, or bucket-level arrangement of WORM as well as retention attributes. This functionality supplies both data defense, including extra security against unexpected or harmful deletion Home Page as well as ransomware and also governing compliance.
6 Simple Techniques For Ec2 Backup
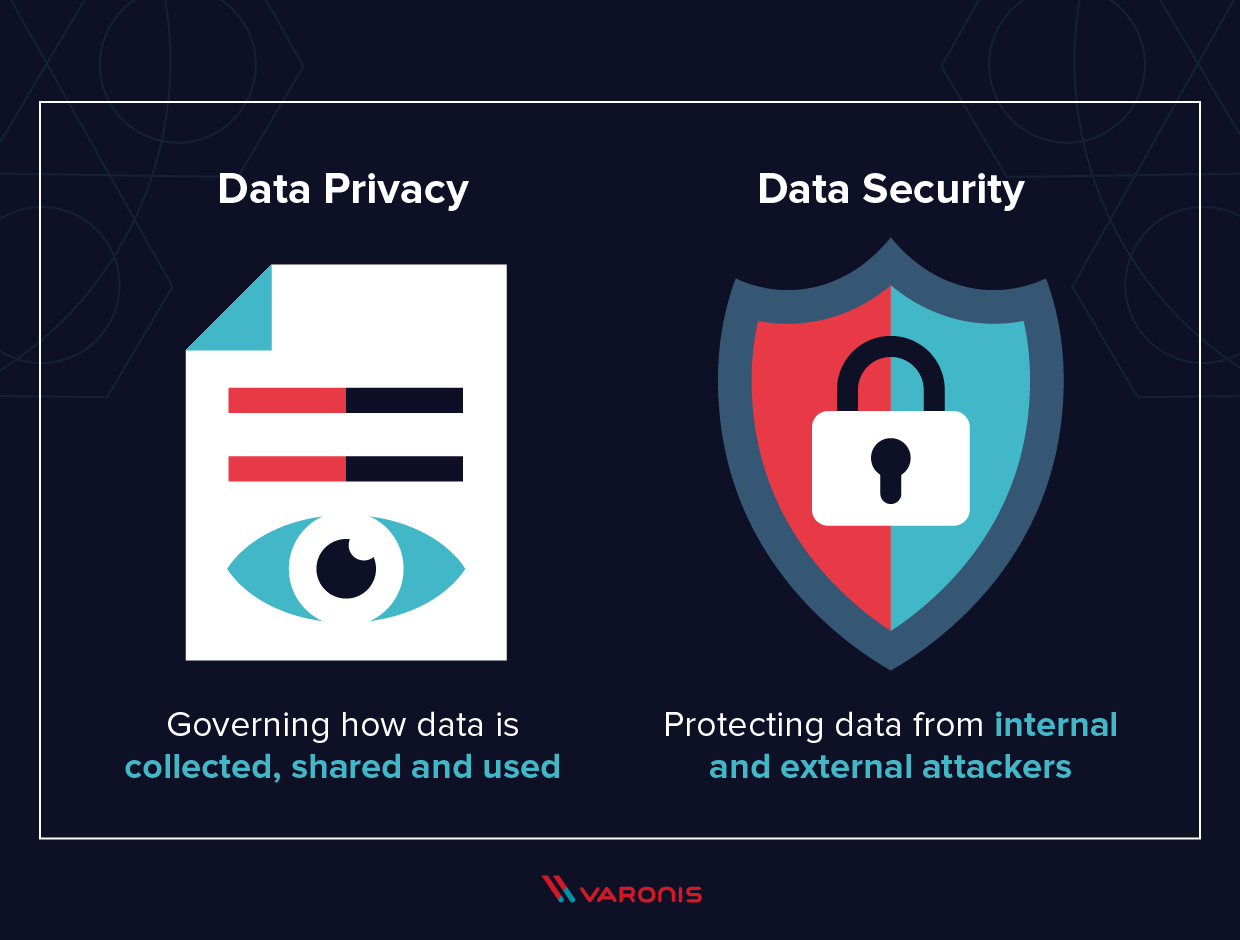
Information defense is the procedure of protecting crucial details from corruption, compromise or loss. The significance of data security boosts as the quantity of information produced as well as saved remains to expand at extraordinary prices. There is also little resistance for downtime that can make it difficult to accessibility important information.

The crucial principles of data protection are to safeguard and also make readily available information under all scenarios.
The Ultimate Guide To Rto
Information lifecycle administration is a comprehensive method for valuing, cataloging and also protecting information assets from application and individual errors, malware as well as virus assaults, maker failing or center blackouts and also disturbances. Extra lately, information monitoring has actually come to consist of finding ways to unlock business worth from otherwise inactive copies of information for reporting, test/dev enablement, analytics and other purposes.(CDP) backs up all the information in a business whenever a change is made. Data portability-- the capability to move data among various application programs, computing settings or cloud services-- provides an additional set of issues and also solutions for information defense.
Some Known Factual Statements About Ransomware Protection
Information defense is the procedure of guarding crucial info from corruption, compromise or loss. The significance of data protection increases as the quantity of data produced and saved proceeds to expand at unmatched rates. There is additionally little resistance for downtime that can make it difficult to gain access to essential info (https://www.mitmoradabad.edu.in/elearning/profile/clumi0/).Protecting information from compromise and also making sure data personal privacy are other vital elements of data protection. The coronavirus pandemic triggered millions of staff members to work from residence, resulting in the demand for remote data security. Businesses need to adapt to ensure they are shielding data any place employees are, from a central information center in the workplace to laptop computers in your home.
The vital principles of data security are to secure as well as make readily available information under all circumstances - http://ttlink.com/clumi0.
Information lifecycle monitoring is a detailed technique for valuing, cataloging and also securing information properties from application as well as user mistakes, malware and infection assaults, machine failing or facility interruptions and disturbances. Much more recently, information management has actually come to include discovering ways to open business worth from or else dormant duplicates of data for coverage, test/dev enablement, analytics and also other objectives.
Not known Details About Rto
(CDP) backs up all the information in a business whenever a change is made. Data portability-- the capability to relocate information amongst various application programs, computing settings or cloud services-- offers one more collection of problems as well as solutions for data defense.Report this wiki page